Connectivity is everywhere
Connectivity & Security
Electronic devices that communicate with each other or with a cloud infrastructure are the basis of the Internet of Things (IoT) and many professional applications. For this, communication must be flexible, fast and secure.
We prepare the basis for this. The modular Ginzinger hardware and software module construction kit offers all the possibilities that a networked world requires. The technical possibilities are complemented by professional security management by Ginzinger and its solution partners and security experts.
CONNECTIVITY
We develop devices that can communicate securely ex works! Together with our partners, we create security for you in technologies, processes and application.
Security for IoT and embedded products
Ginzinger Secure Solutions
01
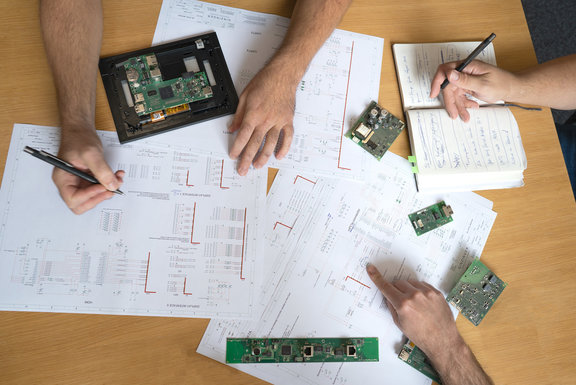
Security by Design
Safe from the start!
A secure implementation usually takes place in 5 steps.
These steps include the necessary analysis and concept development for a successful implementation:
- System and requirements analysis
- Threat analysis
- Risk assessment
- Security concept
- Security implementation
Focus is the selection of the correct technologies and the adapted processes according to the field of application of the product.
02
Security as a process
Safe throughout the entire product life cycle!
We support you in all phases:
- Secure development
- Secure supply chain: material and third-party software
- Secure device provisioning and roll-out
- Secure updates and the appropriate CVE process
- Secure product phase out
Security accompanies our product s throughout their life cycle.

03
Security Technologies
Secure with a wide range of technical solutions
A variety of technically proven methods are available for the flexible hardware and software modular system in order to implement the right level of security.
We offer the following procedures and technology for secure products these include for example:
- Secure OTA Updates
- Software Bill-Of-Material
- Secure Boot
- Secure Authentication
- Hardening
- etc.
04
Experts as partners
Secure through expert knowledge
In a networked product, hardware is only one component of an entire solution chain. In order to think outside the box and implement a secure overall solution, we offer a customized security package for your product solution together with our partners.
As experts in secure industrial and consumer applications, our partners contribute in-depth knowledge of methods and technology.




